The Chaos Beneath Compliance
A few years ago, I thought we were doing well.
ISO certifications? ✔️
GDPR program? ✔️
Risk assessments? Regular and detailed.
But every audit season brought chaos.
Despite all the effort, we were chasing documents, duplicating work, and discovering misalignments late in the game. It wasn’t a knowledge problem it was a structural one. We were managing governance, risk, and compliance (GRC) like isolated checklists, and the cracks were showing.
The Conversation That Changed My Thinking
The turning point came during a conversation with another CISO over coffee.
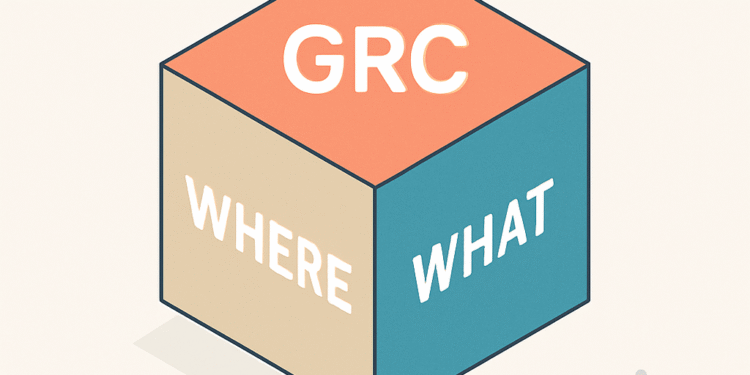
“You’re still thinking in 2D,” he said. “What you need is a cube.”
He introduced me to the concept of the GRC Cube: a simple, three-dimensional model that organizes regulatory obligations across:
- WHERE the rule applies (Jurisdiction)
- WHO it applies to (Industry or function)
- WHAT it focuses on (Security, privacy, continuity, etc.)
That one idea changed everything.
Building the Cube Inside My Organization
Back at the office, I pulled my team into a room and started mapping our compliance requirements. We tagged each framework GDPR, ISO 27001, DORA based on jurisdiction, industry, and focus area.
For example:
- GDPR → EU, all industries, privacy
- DORA → EU, financial sector, resilience/security
- ISO 27001 → Global, all industries, information security

It was like flipping on a light switch.
Suddenly, we could see:
- Where different frameworks overlapped
- Where our controls were duplicated
- Where we had hidden gaps
We weren’t just organizing compliance we were aligning it.
From Fragmentation to Clarity
The benefits came fast. We realized that many of our core controls, such as incident response, access control, and vendor risk, were being managed multiple times under different names. We consolidated them, rewrote a few policies, and created a single, unified control set that could serve multiple frameworks.
Audit fatigue dropped. Evidence was prepared once and reused. Teams finally understood the bigger picture. Instead of preparing separately for ISO 27001, DORA, and GDPR, we designed one approach that fulfilled them all, backed by a cube model that kept everyone aligned.
Teaching Teams to Think in 3D
Perhaps the biggest win was cultural. Before, each team owned its own controls, focused only on “their” regulation. After we introduced the cube, people began thinking across dimensions. Legal teams understood the technical side of controls. IT teams saw why privacy mattered to the board. Executives could now view compliance status across jurisdictions, business units, or focus areas without needing a slide deck for each. The cube became a common language.
How You Can Start Right Now
You don’t need special tools to apply this.
Start simple:
- List every regulatory requirement you manage.
- Tag each one by:
- Jurisdiction (where)
- Audience or industry (who)
- Control focus (what)
- Look for overlaps, gaps, and misalignments.
Once you do this, you’ll stop managing frameworks separately and start managing risk strategically.
The Shift: From Checklists to Clarity
The GRC Cube didn’t just streamline our operations. It changed how I lead. It gave structure to complexity. It helped us evolve from reacting to risk… to designing for resilience.
That’s the real power of the cube. It’s not a framework, it’s a new way of seeing.
So if you’re buried under regulations, trying to lead across silos, or losing time to audit cycles…
Ask yourself three questions:
Where? Who? What?
And start building your cube.
You’ll never look at compliance the same way again.







![Online Scam Cases Continue to Rise Despite Crackdowns on Foreign Fraud Networks [Myanmar] Online Scam Cases Continue to Rise Despite Crackdowns on Foreign Fraud Networks [Myanmar]](https://sumtrix.com/wp-content/uploads/2025/06/30-12-120x86.jpg)





