WhatsApp Launches Private Processing to Enable AI Features While Protecting Message Privacy
WhatsApp Launches Private Processing to Enable AI Features While Protecting Message Privacy
WhatsApp Is Walking a Tightrope Between AI Features and Privacy
WhatsApp Is Walking a Tightrope Between AI Features and Privacy
New Reports Uncover Jailbreaks, Unsafe Code, and Data Theft Risks in top AI Systems
New Reports Uncover Jailbreaks, Unsafe Code, and Data Theft Risks in Leading AI Systems
The essentials of GRC and cybersecurity , How they empower each other
Understanding the connection between GRC and cybersecurity# When talking about cybersecurity, Governance, Risk, and Compliance (GRC) is often considered the...
Fake Security Plugin on WordPress Enables Remote Admin Access for Attackers
Fake Security Plugin on WordPress Enables Remote Admin Access for Attackers
Think Twice Before Creating That ChatGPT Action Figure
Think Twice Before Creating That ChatGPT Action Figure
Why top SOC teams are shifting to Network Detection and Response
Why top SOC teams are shifting to Network Detection and Response
Claude AI Exploited to Operate 100+ Fake Political Personas in Global Influence Campaign
Claude AI Exploited to Operate 100+ Fake Political Personas in Global Influence Campaign
New Research Reveals: 95% of AppSec Fixes Don’t Reduce Risk
New Research Reveals: 95% of AppSec Fixes Don’t Reduce Risk
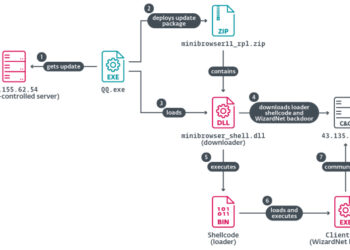
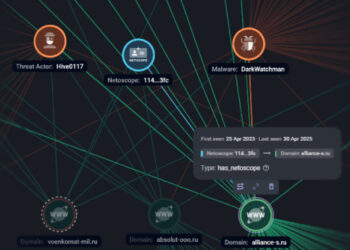
DarkWatchman, Sheriff Malware Hit Russia and Ukraine with Stealth and Nation-Grade Tactics
DarkWatchman, Sheriff Malware Hit Russia and Ukraine with Stealth and Nation-Grade Tactics
Commvault Confirms Hackers Exploited CVE-2025-3928 as Zero-Day in Azure Breach
Commvault Confirms Hackers Exploited CVE-2025-3928 as Zero-Day in Azure Breach
North Korea Stole Your Job
North Korea Stole Your Job
SonicWall Confirms Active Exploitation of Flaws Affecting Multiple Appliance Models
SonicWall Confirms Active Exploitation of Flaws Affecting Multiple Appliance Models
AI Code Hallucinations Increase the Risk of ‘Package Confusion’ Attacks
AI Code Hallucinations Increase the Risk of ‘Package Confusion’ Attacks
Researchers Demonstrate How MCP Prompt Injection Can Be Used for Both Attack and Defense
Researchers Demonstrate How MCP Prompt Injection Can Be Used for Both Attack and Defense
[Free Webinar] Guide to Securing Your Entire Identity Lifecycle Against AI-Powered Threats
Guide to Securing Your Entire Identity Lifecycle Against AI-Powered Threats
Chinese Hackers Abuse IPv6 SLAAC for AitM Attacks via Spellbinder Lateral Movement Tool
Chinese Hackers Abuse IPv6 SLAAC for AitM Attacks via Spellbinder Lateral Movement Tool
Customer Account Takeovers: The Multi-Billion Dollar Problem You Don’t Know About
Customer Account Takeovers: The Multi-Billion Dollar Problem You Don’t Know About














![[Free Webinar] Guide to Securing Your Entire Identity Lifecycle Against AI-Powered Threats [Free Webinar] Guide to Securing Your Entire Identity Lifecycle Against AI-Powered Threats](https://sumtrix.com/wp-content/uploads/2025/04/webinar-play-WXw30Z-350x250.jpg)